today in this tutorial we are going to discuss about (SAST) static application security testing along with its methodologies, types, methods, tools etc. Through this article we will give you a brief overview about SAST and then show you how we can find vulnerabilities in the source code of any web application based on PHP language with the help of kali linux utility called “grep”. Huh. Fine 😁!! So without wasting much time let’s start argle-bargle on static application security testing.
Table of Content
About SAST or Source Code Audit
Difference SAST and DAST
Black and White Box Testing
Installation of bWAAP Vulnerable Application
Source Code Audit with Grep Command
Source Code Audit with EGrep Command
CRASS Tool
Graudit Tool
Overview of RIPS SAST Tool
Questions of Knowledge
Q : What’s is Source Code Analysis or Source Code Audit?
According to the OWASP: Source code analysis or audit, also known as Static Application Security Testing (SAST) Tools, can help analyze source code or compiled versions of code to help find security flaws. SAST is very important for both the organization and us as it helps to analyze source code to detect security vulnerabilities, which make our organization’s applications susceptible to attack, so we need to be aware of all these from the point of view of security potential. Let us show you a small difference between SAST and DAST.
Q : What do you mean by SAST and DAST?
We have given below a small description about both these things.
Static application security testing (SAST) is a set of technologies designed to analyze application source code, byte code and binaries for coding and design conditions that are indicative of security vulnerabilities. SAST is a white box testing method. Its happened in Development Stages.
Dynamic application security testing (DAST) is a black box testing method that examines an application as it’s running to find vulnerabilities that an attacker could exploit.
Q : What is Black Box and White Box Testing?
Both SAST and DAST techniques are also known as white box and black box testing.
Black Box Testing refers to any type of software test that examines an application without knowledge of the internal design, structure, or implementation of the software project.
White Box Testing is a type of testing where the tester can see the code. Testers use this testing method to verify the flow of inputs and outputs through the application, improving usability and design and strengthening security.
Let’s move on to the installation part of the vulnerable application 😁 !!
bWAAP Vuln WebApp Installation
bWAPP, or a buggy web application, is a free and open-source deliberately insecure web application. bWAPP is a PHP application that uses a MySQL database. It can be hosted on Linux/Windows with Apache/IIS and MySQL. Configuring this vulnerable application in any operating system is quite simple that all we have to do is download this application by the link given below, unzip it and move all the files to the apache directory and that’s it.

Now you can check whether all files are unzipped or not by going to the apache directory with the help of the below command.

What is Grep Utility?
Grep is a command-line utility for searching plain-text data sets for lines that match a regular expression. Its name comes from the ed command g/re/p (globally search for a regular expression and print matching lines), which has the same effect.
Hmm 😁 !! We think you should know about some basic commands of the grep utility before jumping to the source code review, so we have given some basic commands below which will facilitate you to use grep utility during SAST audit.
grep Basics Commands:
- grep boo /etc/passwd: basic command to find word into the file.
- grep ‘word’ filename : use to find specific word in the file.
- grep -c ‘root’ frontpage.txt: count words present in the file.
- grep -n “root” /etc/passwd: line number within its input file.
- grep -i ‘bar’ file1: To find case-insensitive ex: bar, Bar, BAR,
- grep -r “192.168.1.5” /etc/ : ecursively i.e. read all files under each directory.
- grep -R ‘passwd’ /etc/: find word into the file or directory or its subdirectory.
- grep –color ‘root’ /etc/passwd: print output with color
Now we will start Source Code Audit with Grep Command. Excited !! Let’s do it.
Find EXEC() System Call
OK :)!! We have first taken a basic example as you can see in the image below. The “exec” system call is used to execute a file that is residing in an active process and “-or” is used to find the “exec” system call into all PHP files of the web project. So we will use the following command that will fetch all “exec(“ system calls from PHP files and print to the terminal. Why have we done this? Because there are a lot of developers who don’t sanitize user input and directly use that input and can allow attackers for such RCE attacks.
grep <syntax> <string want to find> <file path of webapp>

Color Output
There is simple method to print colored output on terminal with given command. By using the “–color” pattern in the command, we can highlight our output.

Find Exec() Function in Specific Files
To find the “exec(“ system call function in any specific extension files like .php, .xml, .txt etc., we can use the include pattern of grep utility. As you can see in the below image which php files is that in which “exec(“ function is being used.

Find Sensitive Credentials
Sometimes developers forgot to remove the credentials from the source code of web application which makes the web application vulnerable. We can try to find the sensitive credentials available in the source code files with the help of command given below. The following command will search the password string in “.xml” extension files and print it to the terminal if it finds anything.

Likewise, we can try to find some others sensitive credentials like login, users, password, api keys etc.

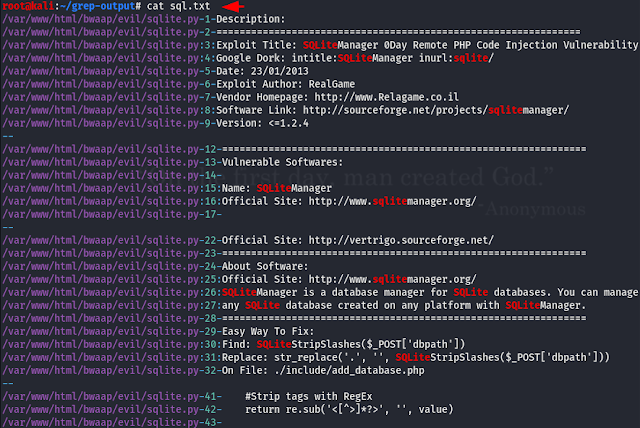
Using “grep” Utility with “cat” Command
Cat is another tool comes pre-installed in kali linux in order to edit or create files. cat which simply send the contents of the file to standard output, which shows up on the standard input of the grep, because the shell has connected the two with a pipe. As you can see below that with the help of these two combinations, we can print the exact output on the terminal.

Monitoring MySQLi query Function
The query() / mysqli_query() function performs a query against a database. If we want to analysis the process of sql queries then we have to findout all the “query(.” funcations by using the command below.

Find eval() Functions
The eval() function evaluates a string as PHP code. Usually, this function is useful for storing PHP code in a database but due to not having proper sanitizing it could give remote code execution permission to the attackers.

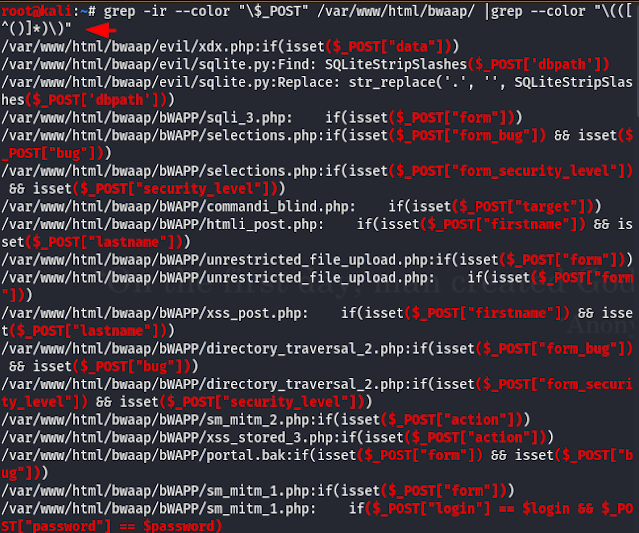
Identify User Supplied Input
In PHP user-supplied input is mostly handled by either $_GET, $_POST, $_COOKIE, or $_REQUEST. However user-supplied input can also be handled with $_FILES, $_SERVER and others. The command we will use to search for user-supplied input within the “$_GET” param.


Count of Number of Matches
We can find the number of lines that matches the given string/pattern.


 Let’s move on to another utility of kali Linux “egrep”. 😁 !!
Let’s move on to another utility of kali Linux “egrep”. 😁 !!What is egrep?
egrep is an acronym for “Extended Global Regular Expressions Print“. It is a program that scans a specified file line by line, returning lines that contain a pattern matching a given regular expression. The difference between grep and egrep is that grep is a command that allows searching content according to the given regular expression and displaying the matching lines while egrep is a variant of grep that allows to search content by applying extended regular expressions to display the machining lines.
Find Shell Functions with egrep Tool
This command searches all PHP files in a directory for vulnerable shell functions.


It can be useful for finding XSS vulnerabilities in PHP code.






Steps to Analysis Source Code
1. You have to given the path of source code project.
2. Select the “vulntype” to “all” and that’s it nothing to do anything more.
As soon as we click on scan it takes a few seconds to analyze the source code written in PHP and then show us depth details about the vulnerabilities identified.Let’s take some questions too 😁 !!
Q: Which command would you prefer if you want to find the user supplied input in the entire PHP source code project along with file name?
















0 Comments